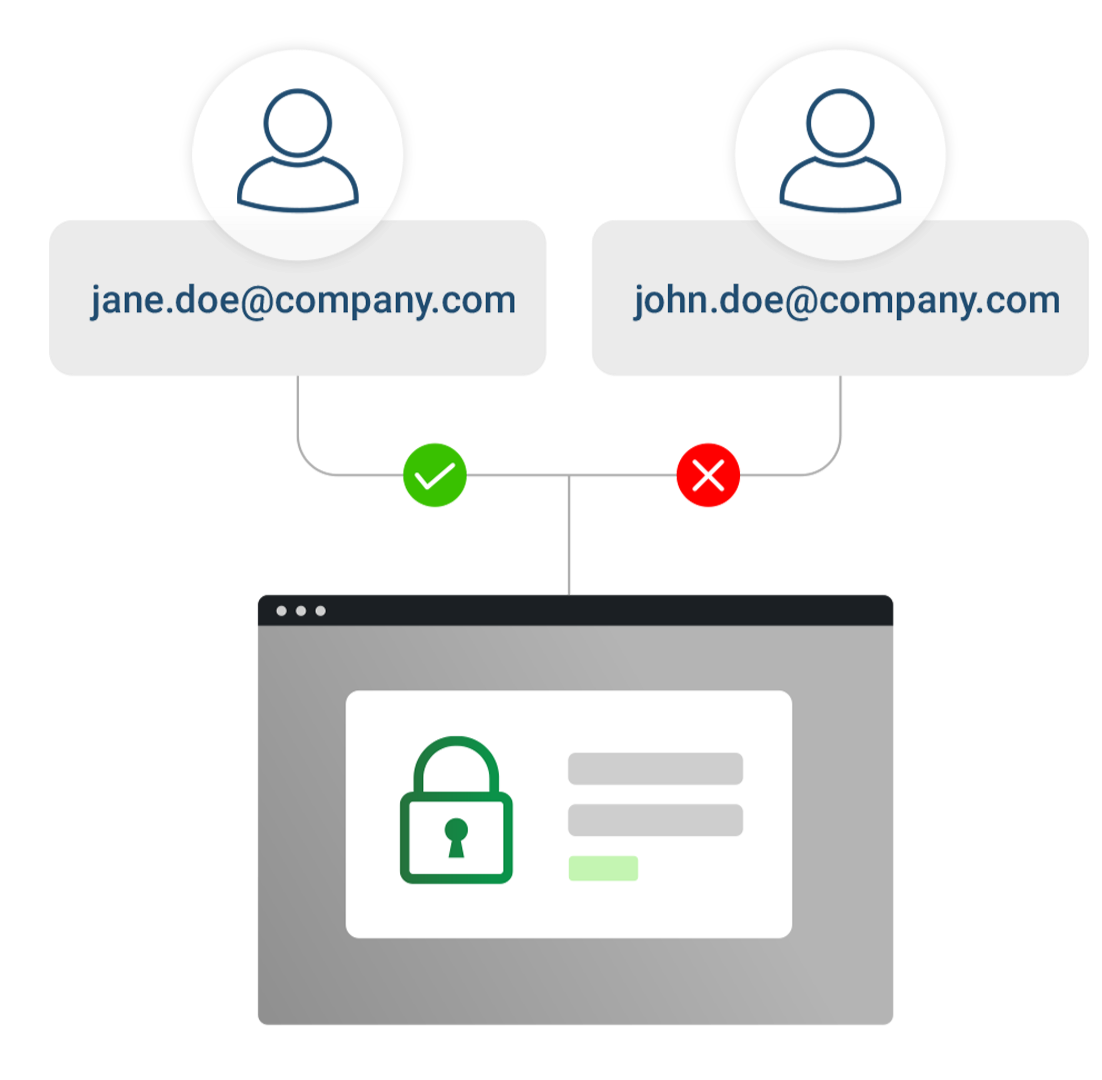
Grant Permissions Without Compromises
Keep the right users in control with access to applications and resources and under the right conditions.
Grant Permissions Without Compromises
Keep the right users in control with access to applications and resources and under the right conditions.

Maximize Security for Administrators & Sensitive Systems
Competitors typically vault passwords, rotate credentials, and record sessions. These are important, but attackers know how to exploit gaps once privileged access is granted.
Zero Trust Identity® enforces phishing-resistant MFA at login and then applies continuous monitoring throughout the session. Behavior analytics and adaptive step-up make sure admins, operators, and even automated services never exceed their intended privileges.
Need privileged access that prevents misuse before it happens?
Core Controls
Password vaulting, rotation, and session recording for accountability.
Just-In-Time Access
Time-limited and approval-based elevation reduces standing privilege.
Continuous Oversight
Real-time risk analysis and anomaly detection prevent misuse mid-session.
Unified Identity
BioThenticate® protects human administrators, while PangaeAPI® secures machine credentials in OT, cloud, and CI/CD pipelines.
Compliance Ready
Audit logs and monitoring support the strictest regulatory standards.