The total identity assurance platform designed to enforce the principle of "never trust, always verify" across your digital ecosystem.

The total identity assurance platform designed to enforce the principle of "never trust, always verify" across your digital ecosystem.

A Unified Defense for the Modern Enterprise
Go beyond static, traditional MFA with dynamic, continuous risk assessment that enables you to adapt to threats in real-time.
Embrace a Passwordless Future
Establish strong identity with passwordless authentication, ensure only validated devices are accessing your network, and secure API integrations.
Secure API Integrations
Our intuitive, real-time dashboard provides a single source of all the information your team needs to effectively manage and monitor integrations.
Automate Security Programs
Automate threat investigation and remediation workflows, minimizing response times and reducing the impact of security incidents.
Cyber Threats are Evolving. Can Your Solution Keep Up?
86% of Breaches
involve compromised credentials with roughly 50% of victims using legacy MFA solutions.
292 Days
The amount of time breaches caused by stolen credentials took to be identified and contained in 2024.
90% of Attacks
begin with phishing attempts, and 87% of these threats hide in encrypted traffic (HTTPS).
$10.22 Million
The average cost of a data breach for U.S. organizations in 2025, significantly higher than the global average of $4.44 million.
Stop breaches with an identity platform that's stronger, safer, and easier to use than legacy MFA solutions.
Empower Your Security Team with Zero Trust Identity
Your holistic suite of tools designed to validate trust at every interaction.
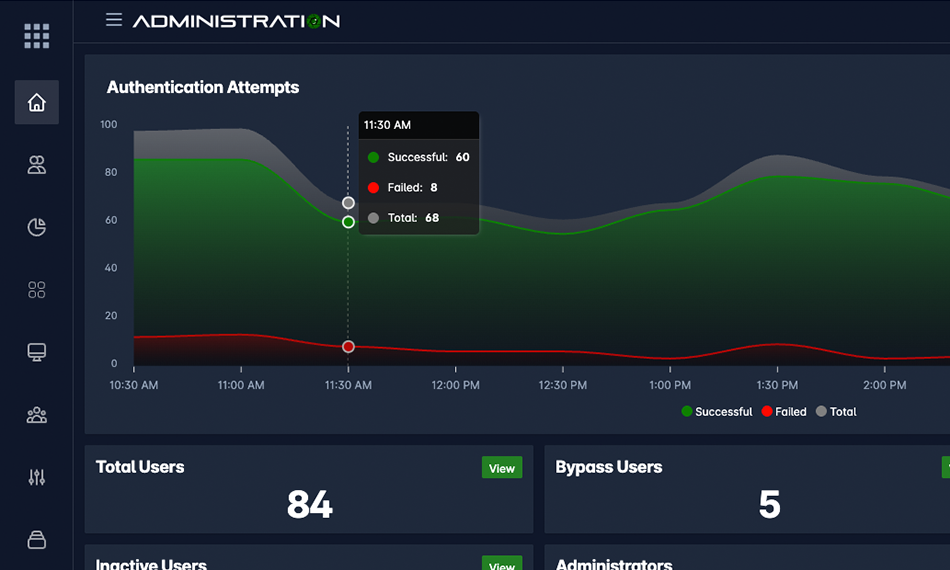
Increased Authentication Visibility
Move from Assumptions to Granular Insights
Eliminate blind spots with a centralized view of every access request across your ecosystem. Our platform provides detailed telemetry on device health, user context, and authentication methods, ensuring you know exactly who is connecting—and how—at all times.
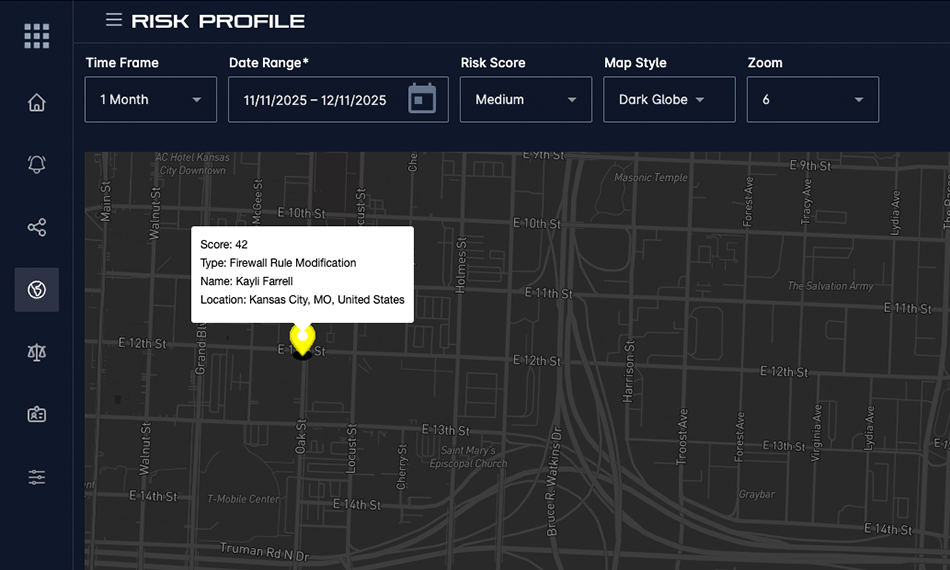
Geolocation of Login Attempts
Pinpoint Access Origins in Real-Time
Automatically flag and block access attempts from high-risk regions or unverified locations. By visualizing the physical source of every login, you can instantly detect anomalies and enforce strict geo-fencing policies to keep threats out.
Multimodal & Layered Biometrics
Defend Against Spoofing with Advanced Identity Proofing
Move beyond static passwords by leveraging multiple biological markers, such as facial recognition, voice analysis, and liveness detection. This layered approach ensures that access is granted only to the actual human behind the device, rather than a bot or a stolen credential.
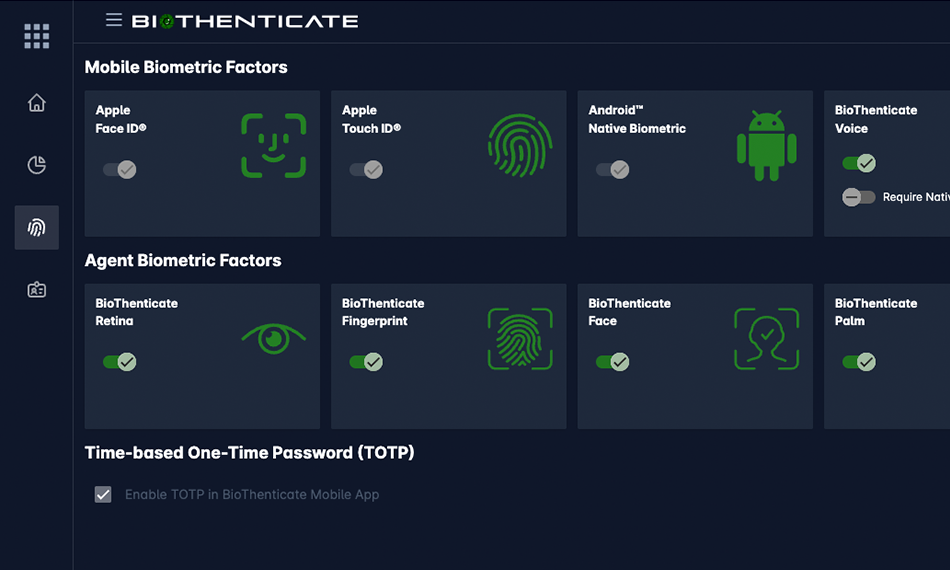
Seamless Integration
Enhance Your Existing Stack without The Friction
Deploy Zero Trust capabilities effortlessly alongside your current IAM, MFA, and PAM providers. Our platform is architected to layer on top of your existing infrastructure via robust APIs, delivering upgraded security without the need for a costly "rip and replace" operation.

Continuous Authentication
Verify Identity Throughout the Entire Session
True Zero Trust doesn’t stop at the front door; it requires validating identity continuously. We monitor biometric and behavioral signals for the full duration of the user session, instantly revoking access if the risk score changes or if the authorized user steps away.
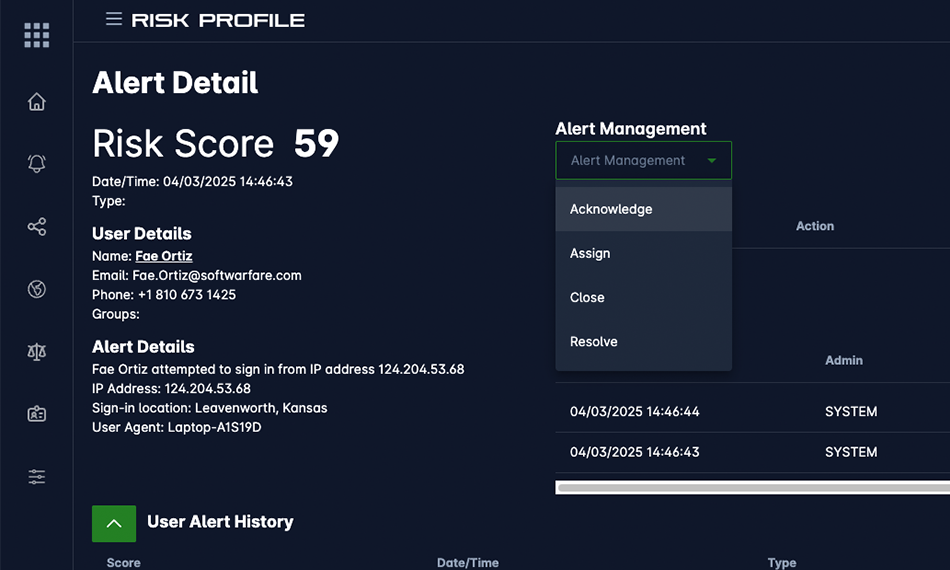
Device Validation
Trust the Device, Not Just the User
Before a user even logs in, Zero Trust Identity validates the device's hygiene. If an endpoint doesn't meet your security policy, access is preemptively blocked—eliminating vulnerabilities inherent to unmanaged devices.

Continuous Authentication
Verify in Real-Time
Identity is dynamic. Zero Trust Identity continuously monitors risk signals throughout the entire session. If context changes, security levels are dynamically adjusted in real-time to neutralize attacks.

Risk Engine
Smarter Detection with Dynamic Prevention
Infuse your strategy with intelligence. Zero Trust Identity's risk engine ingests real-time identity data to calculate risk scores on the fly, powering a security posture that adapts to threats as they emerge.
Automated Response
Immediately Isolate Threats
When a compromise is detected, you can't afford to wait. Utilize automated identity threat response (iDXDR™) to instantly terminate sessions, de-authenticate users, or step-up requirements without human intervention.