Help Us Define the Future of Identity Security
Join SOFTwarfare in protecting U.S. commercial enterprises and critical government sectors from today's cyber threats.
Strong Team. Stronger Culture.
Retaining top talent is one of our top priorities. As a result, SOFTwarfare is one of Kansas City's greatest companies to work for. Our accelerated growth coincides with the broadening perception of Kansas City as a hotbed for cybersecurity talent. At the same time, we
SOFTwarfare is proof that world-class cybersecurity talent thrives in the Midwest. Our rapid growth is driven by a culture that values people just as much as performance. We value open communication, leadership that is easy to reach, and a healthy work-life balance. By recognizing every contribution, we have built a place where top talent doesn’t just work; they belong.
Innovative
Placeholder text. Placeholder text. Placeholder text. Placeholder text. Placeholder text. Placeholder text.
Disciplined
Placeholder text. Placeholder text. Placeholder text. Placeholder text. Placeholder text. Placeholder text.
Collaborative
SOFTwarfare participates in the Department of Defense SkillBridge program and recruits on a rolling basis based on business needs.
Open Positions
AI/ML & Cybersecurity Mission Fellow (SkillBridge)
Move from Assumptions to Granular Insights
Eliminate blind spots with a centralized view of every access request across your ecosystem. Our platform provides detailed telemetry on device health, user context, and authentication methods, ensuring you know exactly who is connecting—and how—at all times.
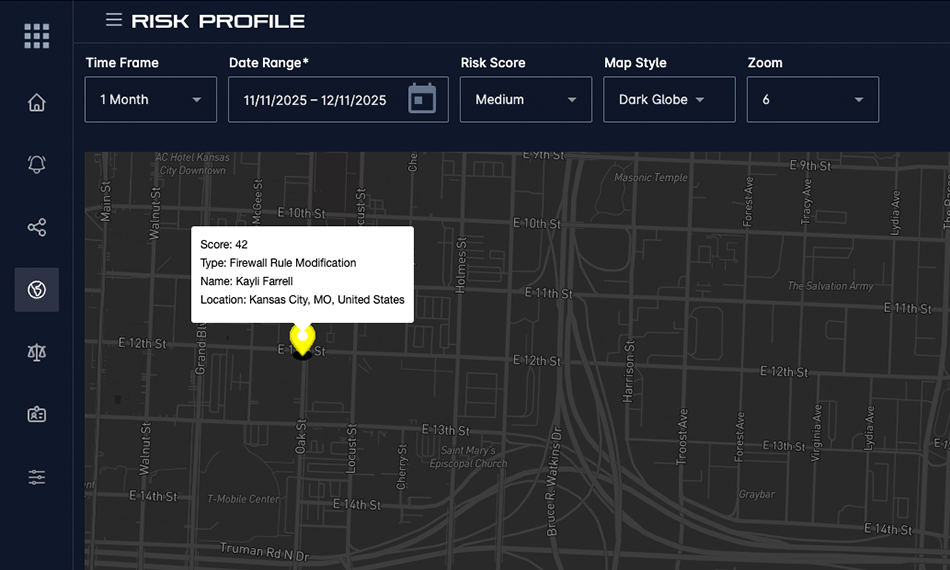
Geolocation of Login Attempts
Pinpoint Access Origins in Real-Time
Automatically flag and block access attempts from high-risk regions or unverified locations. By visualizing the physical source of every login, you can instantly detect anomalies and enforce strict geo-fencing policies to keep threats out.
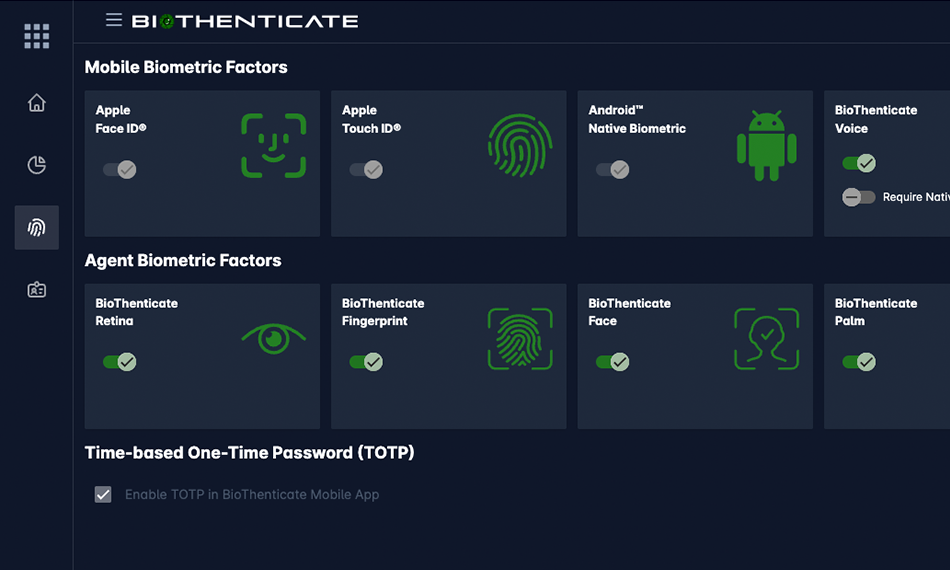
Multimodal & Layered Biometrics
Defend Against Spoofing with Advanced Identity Proofing
Move beyond static passwords by leveraging multiple biological markers, such as facial recognition, voice analysis, and liveness detection. This layered approach ensures that access is granted only to the actual human behind the device, rather than a bot or a stolen credential.
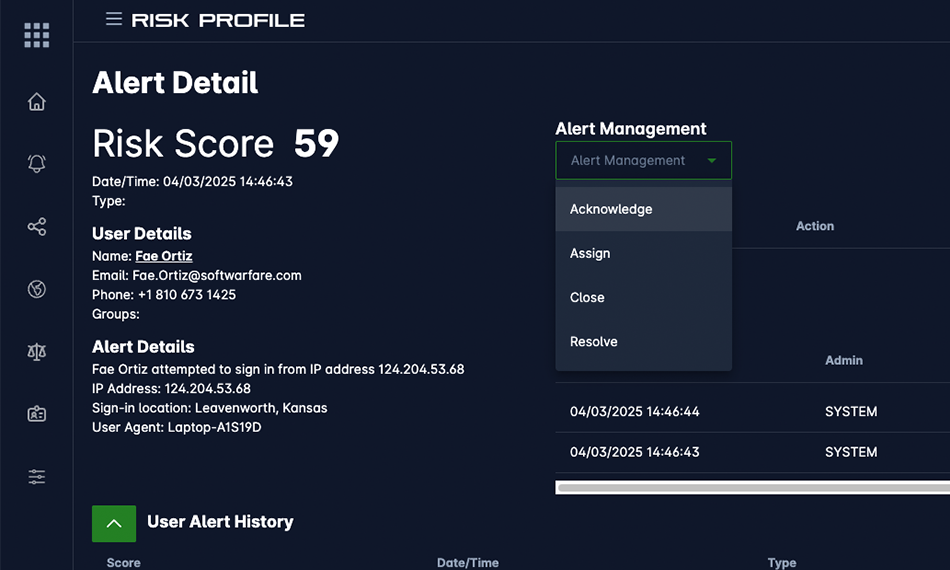
Seamless Integration
Enhance Your Existing Stack without The Friction
Deploy Zero Trust capabilities effortlessly alongside your current IAM, MFA, and PAM providers. Our platform is architected to layer on top of your existing infrastructure via robust APIs, delivering upgraded security without the need for a costly "rip and replace" operation.

Continuous Authentication
Verify Identity Throughout the Entire Session
True Zero Trust doesn’t stop at the front door; it requires validating identity continuously. We monitor biometric and behavioral signals for the full duration of the user session, instantly revoking access if the risk score changes or if the authorized user steps away.
Become a tech alliance or development partner.
Strong partnerships lead to strong security platforms. That’s why our products and solutions are driven in large part by seamlessly integrating best-in-class cyber security technologies. The result is an unmatched ecosystem of partners tailored to fit the specific needs of each customer.
Get the support and partnership resellers need.
We are constantly fostering relationships with trusted security advisors. That’s why we created a customizable platform to ease the pains of integrating your customer’s most critical cyber security applications.
Already a reseller?