Trust Nothing. Verify Everything.
Enforce the principle of "never trust, always verify" across your digital ecosystem.
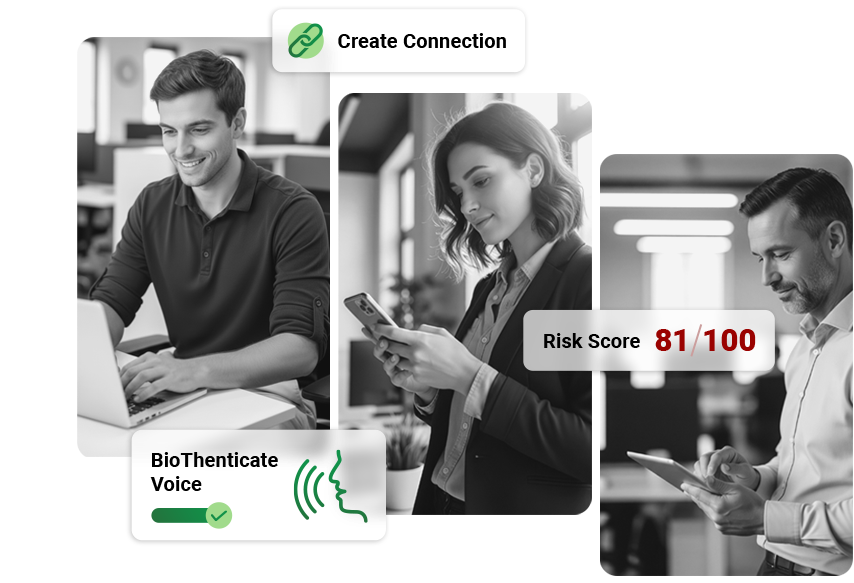
Embrace a Passwordless Future
Establish strong identity with passwordless authentication, ensure only validated devices are accessing your network, and secure API integrations.
Secure API Integrations
Our intuitive, real-time dashboard provides a single source of all the information your team needs to effectively manage and monitor integrations.
Automate Security Programs
Automate threat investigation and remediation workflows, minimizing response times and reducing the impact of security incidents.
Achieve 100x Stronger Identity Confidence Over Legacy MFA Solutions
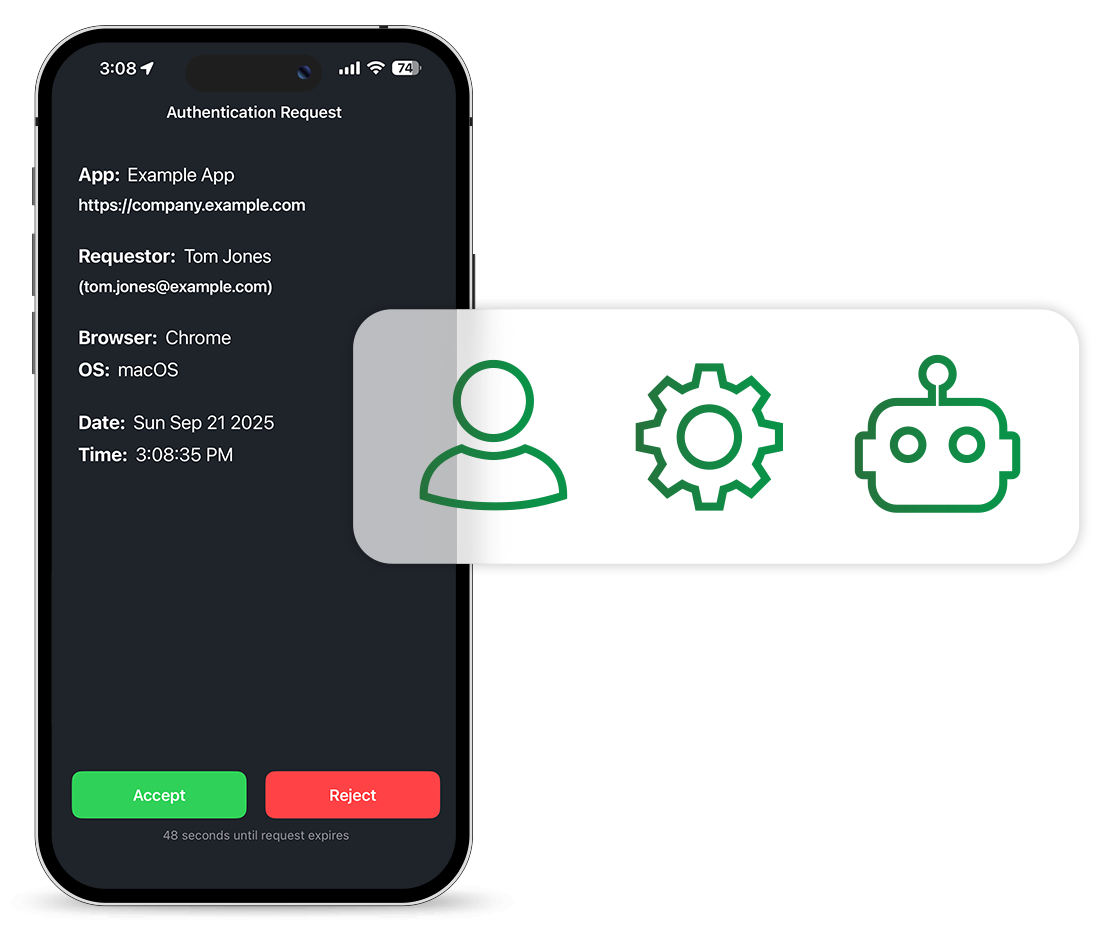
Authenticate Every Identity
Move beyond the network perimeter. Our platform uses industry-leading, high-security authentication to validate every human and machine identity at every access request. By removing implicit trust, we ensure only the right users get in.
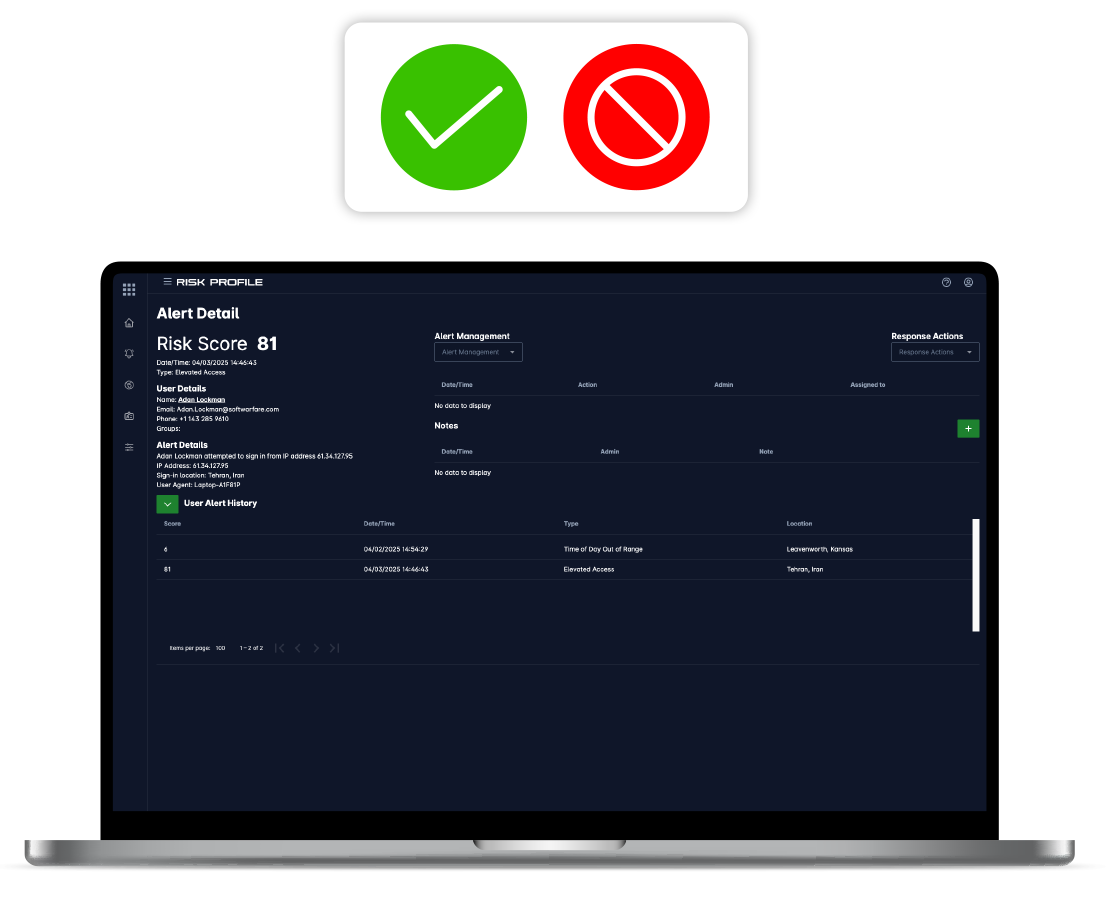
Enforce Context-Aware Access
Create and enforce granular security policies based on a user's role, location, and device security posture. Our lightweight, configurable methods empower you to adapt access rules in real-time, strengthening security without impacting your bottom line.

Enforce Context-Aware Access
Create and enforce granular security policies based on a user's role, location, and device security posture. Our lightweight, configurable methods empower you to adapt access rules in real-time, strengthening security without impacting your bottom line.
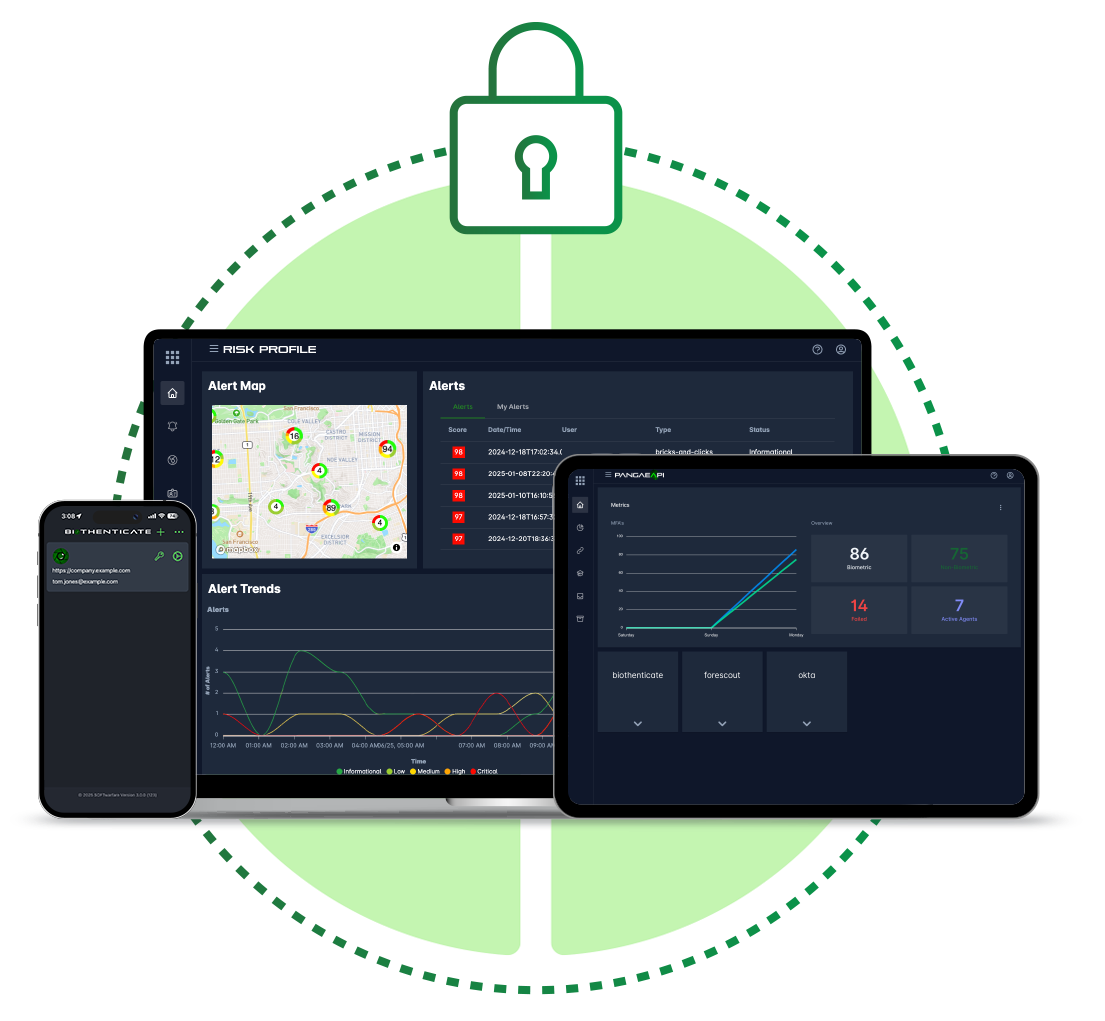
A Unified Platform
Create and enforce granular security policies based on a user's role, location, and device security posture. Our lightweight, configurable methods empower you to adapt access rules in real-time, strengthening security without impacting your bottom line.
Authenticate Every Identity
Move beyond the network perimeter. Our platform uses industry-leading, high-security authentication to validate every human and machine identity at every access request. By removing implicit trust, we ensure only the right users get in.
Enforce Context-Aware Access
Create and enforce granular security policies based on a user's role, location, and device security posture. Our lightweight, configurable methods empower you to adapt access rules in real-time, strengthening security without impacting your bottom line.
A Unified Platform
This is the text area for this paragraph. Once you've added your content, you can customize its design by using different colors, fonts, font sizes and bullets.
This is a paragraph to describe your story. To change it, simply click and start typing.
Title or Question
Describe the item or answer the question so that site visitors who are interested get more information. You can emphasize this text with bullets, italics or bold, and add links.Title or Question
Describe the item or answer the question so that site visitors who are interested get more information. You can emphasize this text with bullets, italics or bold, and add links.Title or Question
Describe the item or answer the question so that site visitors who are interested get more information. You can emphasize this text with bullets, italics or bold, and add links.