One platform to enforce the principle of "never trust, always verify" across your digital ecosystem.


One platform to enforce the principle of "never trust, always verify" across your digital ecosystem.

Embrace a Passwordless Future
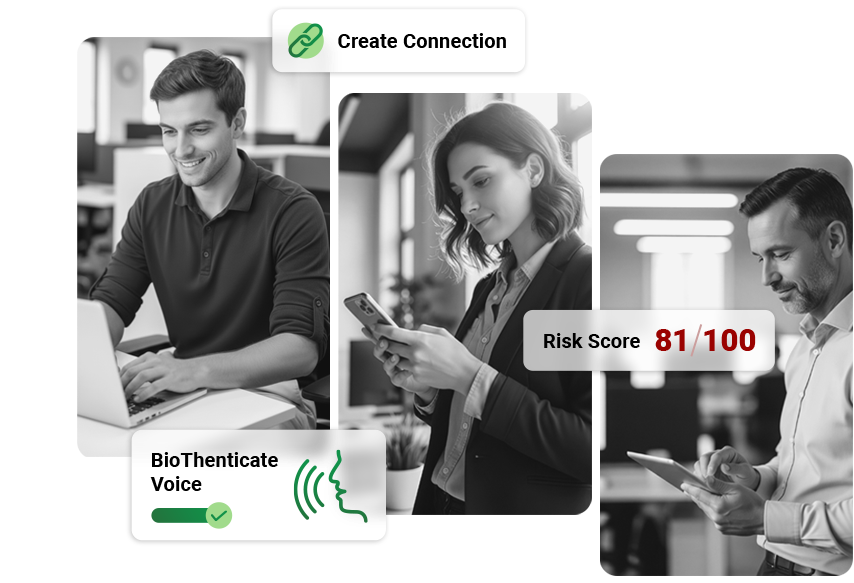
Establish strong identity with passwordless authentication, ensure only validated devices are accessing your network, and secure API integrations.
Secure API Integrations
Our intuitive, real-time dashboard provides a single source of all the information your team needs to effectively manage and monitor integrations.
Automate Security Programs
Automate threat investigation and remediation workflows, minimizing response times and reducing the impact of security incidents.
Embrace a Passwordless Future
Establish strong identity with passwordless authentication, ensure only validated devices are accessing your network, and secure API integrations.
Secure API Integrations
Our intuitive, real-time dashboard provides a single source of all the information your team needs to effectively manage and monitor integrations.
Automate Security Programs
Automate threat investigation and remediation workflows, minimizing response times and reducing the impact of security incidents.
Achieve 100x Stronger Identity Confidence Over Legacy MFA Solutions
Achieve 100x Stronger Identity Confidence Over Legacy MFA Solutions

Device Validation
Minimize your attack surface by preventing insecure devices from accessing sensitive resources.
- Preemptively block untrusted access by verifying device trust for every session.
- Enforce device-hardened, passwordless authentication for all laptops, desktops, and endpoints.
- Eliminate vulnerabilities inherent to traditional MFA by ensuring every connecting device meets your security policy.
Continuous Authentication
Dynamically adjust authentication requirements in real time based on risk signals.
- Continuously verify identity throughout each session, not just at the point of initial access.
- Dynamically adapt security levels based on real-time context and risk signals.
- Achieve security 100 times stronger than legacy MFA, effectively neutralizing phishing and Man-in-the-Middle (MITM) attacks.


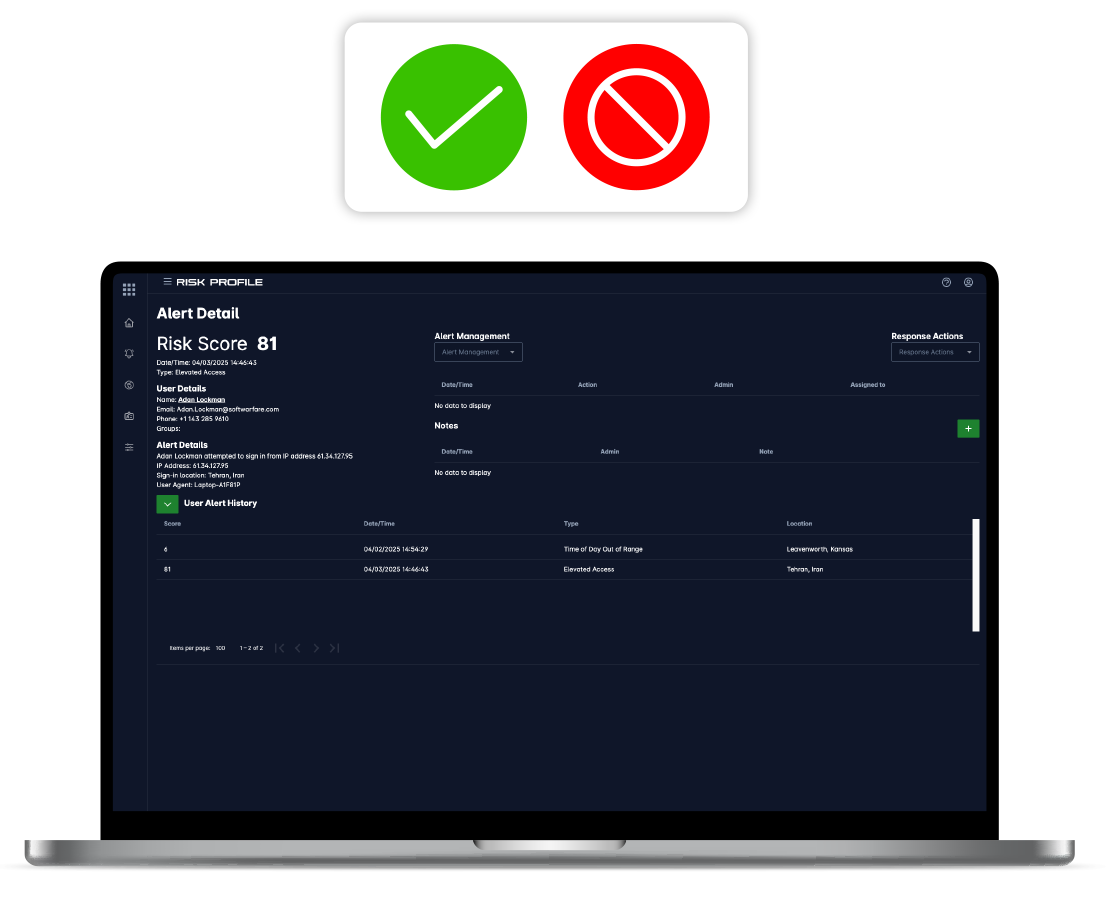
Risk Engine
Minimize your attack surface by preventing insecure devices from accessing sensitive resources.
- Infuse dynamic identity data into your detection strategy to accurately assess risk in real time.
- Power a continuous and risk-based security posture that is driven by your organization's policies.
- Provide real-time threat response capabilities that competing solutions cannot match.
Response
Human-in-the-loop or automated response provides de-authentication, session termination and/or step-up authentication capabilities.
- Utilize Automated Identity Threat Response (iDXDR™) to immediately identify and isolate threats linked to identity compromise.
- Enhance the speed and accuracy of threat isolation and remediation.
- Immediately neutralize threats linked to identity compromise to secure the entire ecosystem, from enterprise users to OT devices.


- Preemptively block untrusted access by verifying device trust for every session.
- Enforce device-hardened, passwordless authentication for all laptops, desktops, and endpoints.
- Eliminate vulnerabilities inherent to traditional MFA by ensuring every connecting device meets your security policy.

Device Validation
Minimize your attack surface by preventing insecure devices from accessing sensitive resources.
- Continuously verify identity throughout each session, not just at the point of initial access.
- Dynamically adapt security levels based on real-time context and risk signals.
- Achieve security 100 times stronger than legacy MFA, effectively neutralizing phishing and Man-in-the-Middle (MITM) attacks.

Continuous Authentication
Dynamically adjust authentication requirements in real time based on risk signals.

- Infuse dynamic identity data into your detection strategy to accurately assess risk in real time.
- Power a continuous and risk-based security posture that is driven by your organization's policies.
- Provide real-time threat response capabilities that competing solutions cannot match.

Risk Engine
Minimize your attack surface by preventing insecure devices from accessing sensitive resources.
- Utilize Automated Identity Threat Response (iDXDR™) to immediately identify and isolate threats linked to identity compromise.
- Enhance the speed and accuracy of threat isolation and remediation.
- Immediately neutralize threats linked to identity compromise to secure the entire ecosystem, from enterprise users to OT devices.

Response
Human-in-the-loop or automated response provides de-authentication, session termination and/or step-up authentication capabilities.
Ready to Revolutionize Your Identity Security?
PLATFORM
SOLUTIONS
ENTERPRISE
DEFENSE
COMPANY
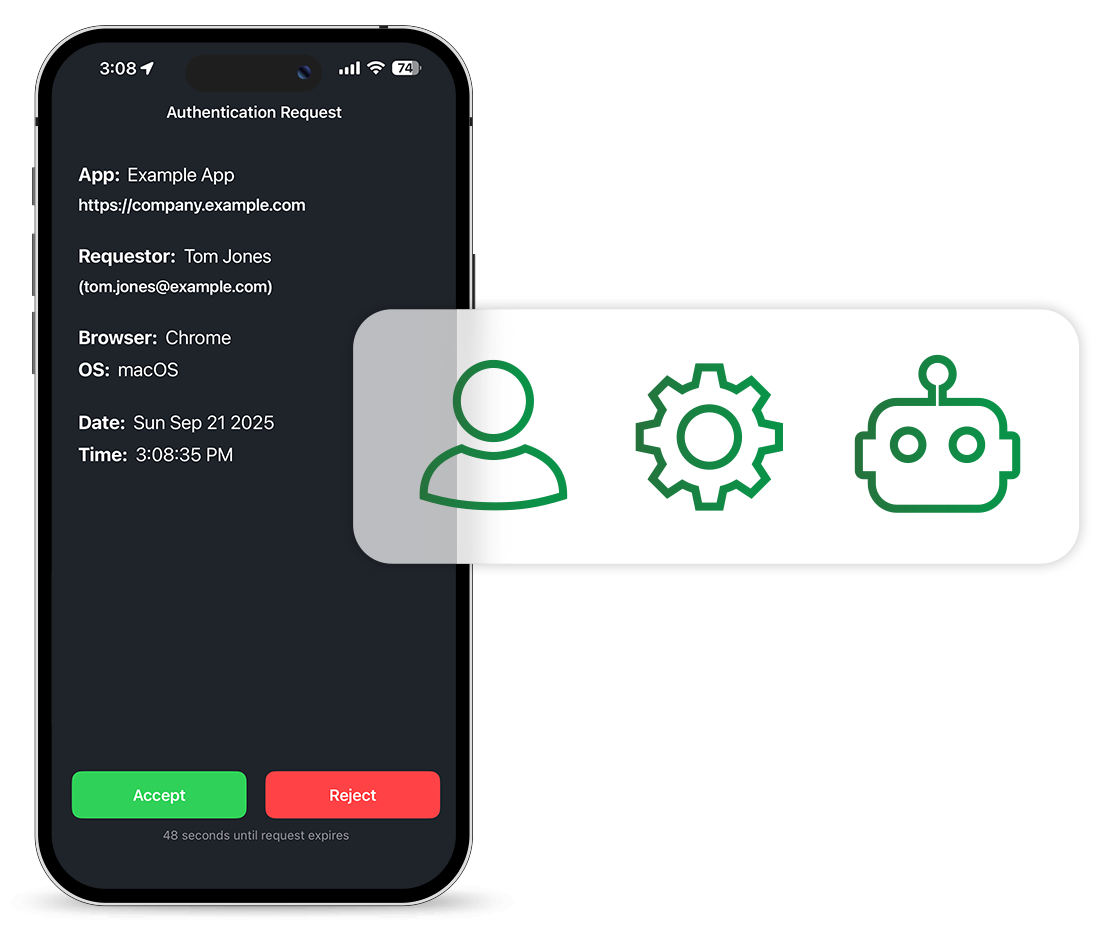
Authenticate Every Identity
Move beyond the network perimeter. Our platform uses industry-leading, high-security authentication to validate every human and machine identity at every access request. By removing implicit trust, we ensure only the right users get in.
Enforce Context-Aware Access
Create and enforce granular security policies based on a user's role, location, and device security posture. Our lightweight, configurable methods empower you to adapt access rules in real-time, strengthening security without impacting your bottom line.
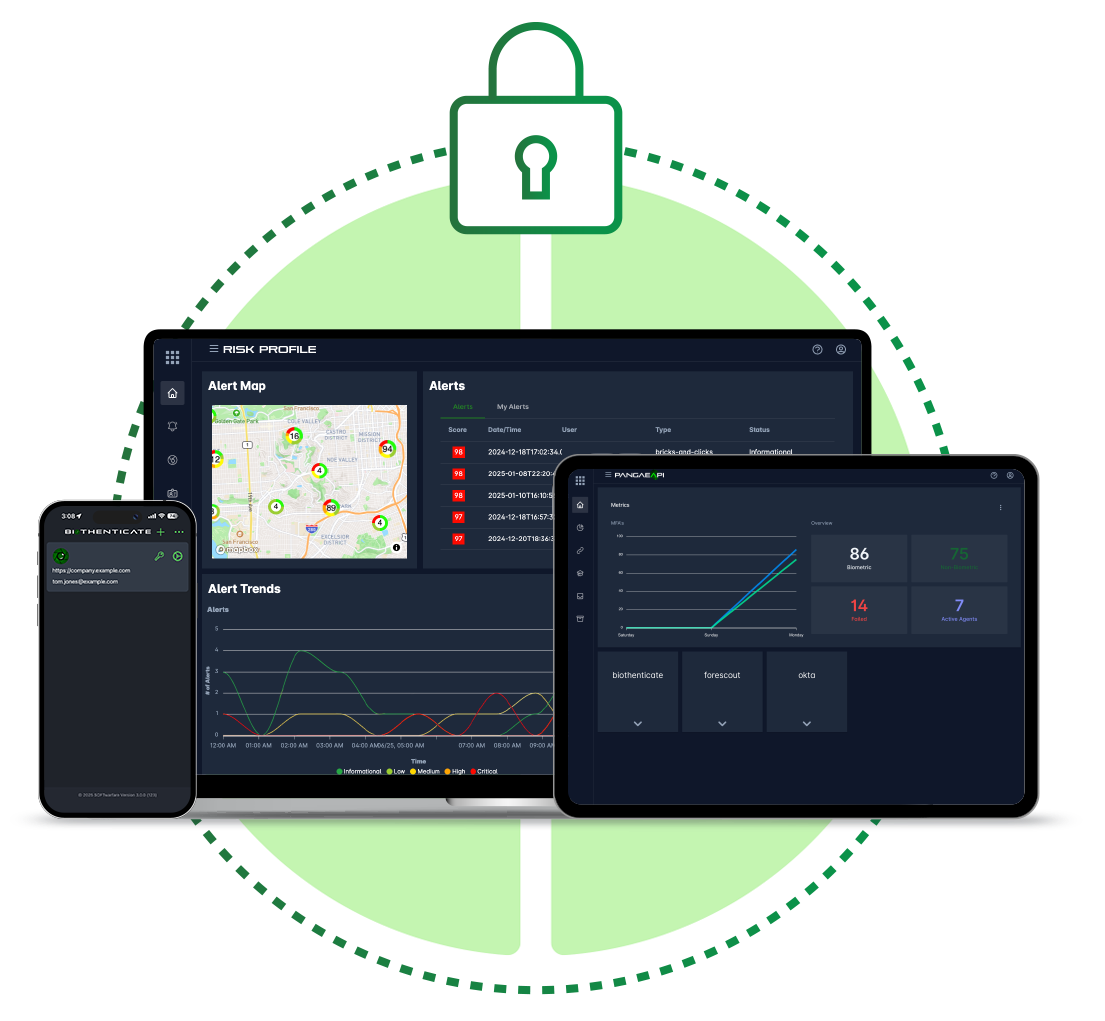
A Unified Platform
Create and enforce granular security policies based on a user's role, location, and device security posture. Our lightweight, configurable methods empower you to adapt access rules in real-time, strengthening security without impacting your bottom line.
Authenticate Every Identity
Move beyond the network perimeter. Our platform uses industry-leading, high-security authentication to validate every human and machine identity at every access request. By removing implicit trust, we ensure only the right users get in.
Enforce Context-Aware Access
Create and enforce granular security policies based on a user's role, location, and device security posture. Our lightweight, configurable methods empower you to adapt access rules in real-time, strengthening security without impacting your bottom line.
A Unified Platform
This is the text area for this paragraph. Once you've added your content, you can customize its design by using different colors, fonts, font sizes and bullets.
This is a paragraph to describe your story. To change it, simply click and start typing.
Title or Question
Describe the item or answer the question so that site visitors who are interested get more information. You can emphasize this text with bullets, italics or bold, and add links.Title or Question
Describe the item or answer the question so that site visitors who are interested get more information. You can emphasize this text with bullets, italics or bold, and add links.Title or Question
Describe the item or answer the question so that site visitors who are interested get more information. You can emphasize this text with bullets, italics or bold, and add links.